SonarQube plugin for TIBCO BE projects
Overview
BECS Sonarqube plugin performs static code analysis of TIBCO BusinessEvents (BE) projects or EAR files and sends the code violations and issues to SonarQube server. In addition to analyzing TIBCO BE code base based on BE Code Scanner code violation checks, it provides metrics on the resources and BE rules, rule definitions etc. that can be useful in Function Point Analysis. Behind the scenes, the BECS Sonar plugin calls the command line version or Cloud version of BE Code Scanner.
In a build pipeline in Jenkins, Hudson or any similar CI-CD tools, a static code analysis of TIBCO BE projects can be initiated to run code violation checks and to break the builds if a specific threshold is met like Critical violations etc. When the issues are pushed to SonarQube server, it stores the data in database and displays the results in a very intuitive GUI.
Each analysis performed using BECS Sonarqube plugin is stored as a snapshot by SonarQube in its repository providing the opportunity to trend the code quality of BE projects. Contact us to set up a demo of BE Sonarqube plugin to understand how you can optimize the code quality of your BusinessEvents projects.
Features
Key Features
- Run anywhere: Sonar plugin for BE Code Scanner works on the Sonarqube LTS versions on any OS or any IaaS platform where you run your Sonarqube server. It can interact with your BE Code Scanner on-premise or cloud version deployed anywhere
- Scan Multiple Projects: Sonar BE5CS plugin can analyze single project or multiple projects. You can provide the parent repository path where multiple projects are stored and the BECS Sonar plugin identifies all the BE projects and does code review on them and identifies the issues.
- Summary Metrics: It lists the metrics of BusinessEvents project by providing the number of rules, rule functions, Concepts, Events, Channels, connection resources and global variables
- Vulnerability classification: BECS Sonar plugin identifies the issues based on CWE standards and tags them with the CWE ID. Bugs, vulnerabilities and code smells associated with CWE tag can be filtered using tags.
- Granular issue details and suggestions: BECS Sonar plugin provides detailed analysis of issue, its line identifier in the code, along with recommendations on how to fix the issue in the Issues section.
- Customization: It supports BE Code Scanner rules override fuctionality to provide the path in sonar project properties file or in Project/Global Administration tab to update severity, description etc. and to filter any resources.
Installation
BECS Sonar plugin Installation
Installation for BECS Sonar plugin is similar to BW5CS Sonar plugin installation. Please refer to Installation Steps. As noted in that section, download LTS version of Sonarqube, and BECS Sonar plugin from download portal provided with your enterprise version.
Copy the sonar-ccl-tib-becs-plugin-
TIBCO BE Sonar plugin Configuration
Global Config
- In order to change global config, login as a administrator to Sonarqube server
- Under Administration > Configuration > General Settings CCL BECS Sonar plugin should be listed as shown below.
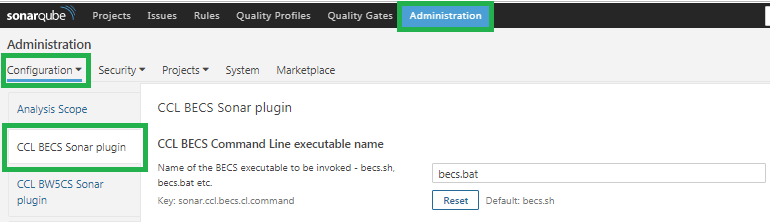
- Based on OS, use becs.bat for Windows or becs.sh for BECS Command Line executable name
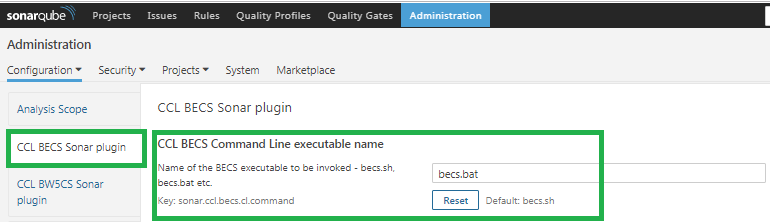
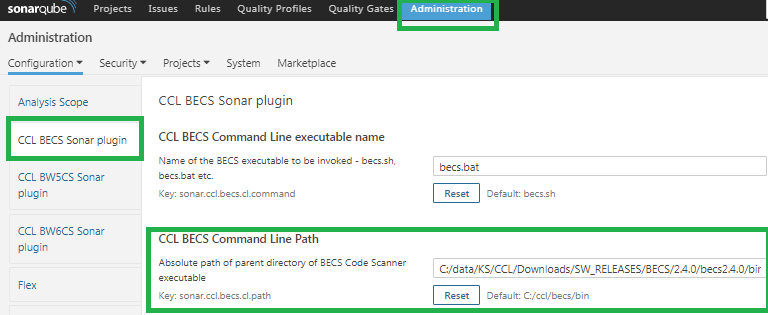
- Also, provide the full path for parent directory for BECS Command Line
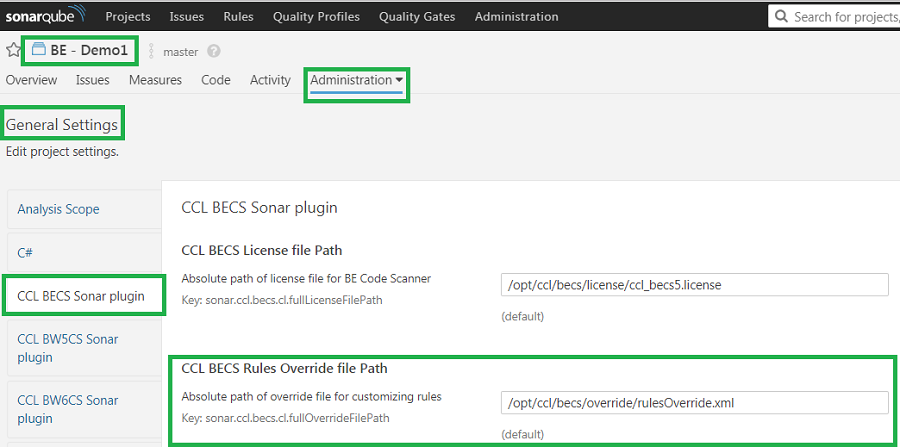
Project Configuration
Project level settings for BECS Sonar plugin can be configured for rules override settings.
- Under Projects > [project name] > Administration > General Settings CCL BECS Sonar plugin and override file options should be visible as shown below.
Running Analysis
To run the analysis, you can use any Analyzer supported by Sonarqube.
sonar-project.properties Setup
# must be unique in a given SonarQube instance
sonar.projectKey=be-project# this is the name and version displayed in the SonarQube UI. Was mandatory prior to SonarQube 6.1.
sonar.projectName=My BE Sonar projectsonar.projectVersion=1.0
# This property is optional if sonar.modules is set.
sonar.sources=.sonar.language=ccltibbe
# Encoding of the source code. Default is default system encoding
sonar.sourceEncoding=UTF-8# CCL BE Plugin options
#Rules override file path. This overrides the default value set on SonarQube Administration GUI
sonar.ccl.cl.fullOverrideFilePath = /opt/ccl/beRulesOverride.xmlPlease refer to SonarQube documentation - Analysis Parameters for different parameters. As an example, if SonarQube is not running locally, sonar.host.url needs to be provided
Sequence of properties evaluation
The sequence of properties evaluation is similar to what is noted in BW5CS Sonarqube plugin - Properties Evaluation Sequence
Project Analysis
Analyzing a project with BECS Sonar plugin is similar to BW5CS Sonar analysis. Please refer to Analyzing the project
Reviewing the Analysis
Analysis review screens might look different based on your version of Sonarqube server. Below snapshorts are from 6.7.x LTS version
- Check the project snapshot after the analysis is complete in Sonarqube server as shown in the image below.
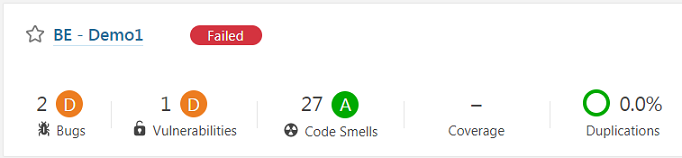
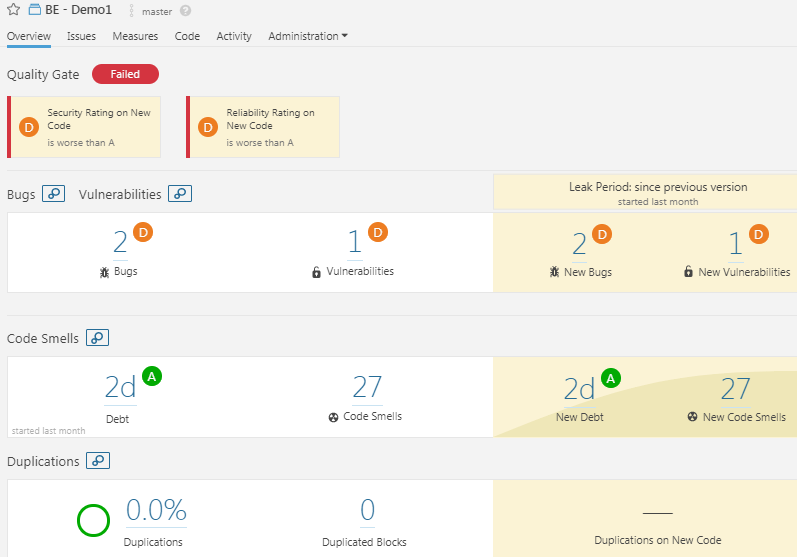
- As per the SonarQube convention, code violations from BE project source code are categorized as Bugs, Vulnerabilities and Code Smells.
- Go to Project overview page by clicking on Project name
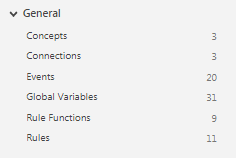
- Number of Rules, Rule Functions, Connections, Global Variables, Concepts, Events and Channels can be viewed by clicking on Metrics tab under General section
- By clicking on Issues tab, you can view all the code violations in the project(s) scanned. Issues have a description with recommendation for fixing, along with details on Rule, Rule definition etc. where the issue occurred. CWE classification is noted in description with the associated CWE-ID. Description can be overridden using rules override file
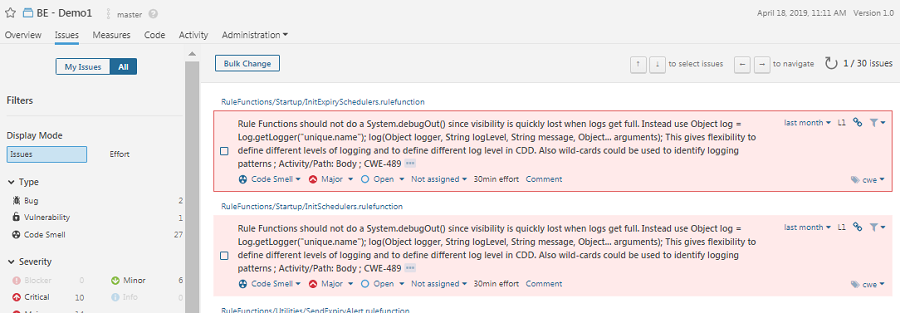
- Toggle different sections like Type as Bug, Vulnerability or Severity for Critical etc. to find associated issues
- Click on cwe under Tags to find all the violations which have CWE classification
- Issues can be assigned to a user, severity can be changed etc. Essentially, standard Sonarqube features are all available for BE project analysis